TLS(Thread Local Storage) Callback 작성 중...........
Reverse Engineering 2023. 1. 22. 22:29 |반응형
작성 중....................
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
|
#include <stdio.h>
#include <Windows.h>
static int v1 = 0;
static int v2 = 0;
VOID WINAPI Tls_callback1(PVOID DllHandle, DWORD Reason, PVOID Reserved)
{
if (Reason == DLL_PROCESS_ATTACH)
v1 = 1;
}
VOID WINAPI Tls_callback2(PVOID DllHandle, DWORD Reason, PVOID Reserved)
{
if (Reason == DLL_PROCESS_ATTACH)
v2 = 2;
}
#pragma comment (linker, "/INCLUDE:__tls_used")
/**** Section 1. Start
TLS callback 함수 등록은 Section 1 이나 Section 2 스타일 모두 가능.
#pragma comment (linker, "/INCLUDE:_p_tls_callback1")
#pragma data_seg(push)
#pragma data_seg(".CRT$XLC")
EXTERN_C PIMAGE_TLS_CALLBACK p_tls_callback1 = Tls_callback1;
#pragma data_seg(".CRT$XLD")
EXTERN_C PIMAGE_TLS_CALLBACK p_tls_callback2 = Tls_callback2;
#pragma data_seg(pop)
Section 1. End ****/
/**** Section 2 Start ****/
#pragma data_seg(push)
#pragma data_seg(".CRT$XLC")
EXTERN_C PIMAGE_TLS_CALLBACK pTLS_CALLBACKs[] = { Tls_callback1, Tls_callback2, 0 };
#pragma data_seg()
#pragma data_seg(pop)
/**** Section 2 End ****/
int main() {
printf("Test values from tls callbacks are: tls1 = %d, tls2 = %d\n", v1, v2);
return 0;
}
|

|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
#include <stdio.h>
#include <Windows.h>
VOID WINAPI Tls_callback(PVOID DllHandle, DWORD Reason, PVOID Reserved)
{
if (Reason == DLL_PROCESS_ATTACH)
if (IsDebuggerPresent())
{
MessageBoxA(NULL, "Debugger present.", "Detector", MB_OK);
exit(-1);
}
}
#pragma comment (linker, "/INCLUDE:__tls_used")
#pragma comment (linker, "/INCLUDE:_p_tls_callback")
#pragma data_seg(push)
#pragma data_seg(".CRT$XLC")
EXTERN_C PIMAGE_TLS_CALLBACK p_tls_callback = Tls_callback;
#pragma data_seg(pop)
int main() {
printf("No debugger present.");
return 0;
}
|
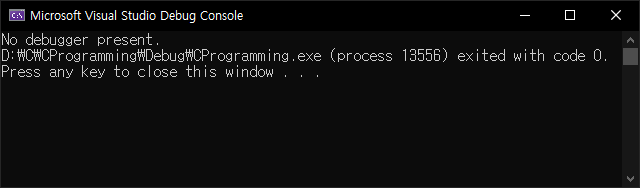

참고
https://blog.naver.com/stop2y/221201916660
반응형
'Reverse Engineering' 카테고리의 다른 글
| Cheat Engine Cuphead Character HP Cheating - 치트 엔진 컵헤드 HP 치팅 (0) | 2023.01.28 |
|---|---|
| Cheat Engine Dosbox Editor making - 치트 엔진 도스박스 에디터 만들기 (0) | 2023.01.26 |
| [x32dbg/x64dbg] Assembly Mnemonic Help 어셈블리 명령어 설명 (0) | 2023.01.20 |
| [x32dbg/x64dbg] Cross References 크로스 레퍼런스 (0) | 2023.01.19 |
| Cheat Engine Address - 치트 엔진 주소 표시 (0) | 2023.01.06 |

